Use A Database Audit Tool For The Database Security Purpose
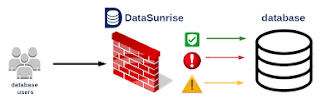
We all know about the financial audit. But, software audit, database audit, etc. are available. An audit program is related to the accountability of an organization. Basically, an audit performance helps to maintain the privacy. So, the database auditing helps to find out the information about the database and protect the database...... Read More