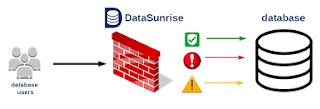
Install A User-Friendly Security Solution
Firewall software is a must to protect all the sensitive information and the important database. Most of the people don’t know about the firewall. They think the anti-virus and firewall are the same software. Actually, No! Both are the very much different and both works in a different way. Antivirus can detect the virus attack, remove the virus, and clean the PC while the firewall software prevents the hackers to hack the system. Read More About This Blog